How to ensure the safety of personnel in dangerous areas during downtime? The use of the "Pocket key" solution provided by Peel Magnetic can prevent the accidental restart of mechanical equipment until the person is out of the danger area.
Before the operator (or more) enters the security area through the security door, it is required to use the "personal key" to authorize and identify the PITreader device on the side of the security door. Only allowed personnel can open the protective lock device and enter the inside. The person's information is then "checked in" to the control system (PNOZmulti2 or PSS4000). The machinery is now shut down and the safety of the personnel is ensured. This assurance comes from the fact that the operator's "personal key" information has been recorded. In order to put the mechanical equipment back into operation, all operators must use their own "personal keys" to carry out the "check out" operation, and ensure that each operator is out of the dangerous area.

The "Pocket key" protection function is implemented using function blocks/modules in the Pilz controllers "PSSu PLC" (PSS 4000) and "PNOZm B1" (PNOZmulti 2).
The functions are described as follows:
A.koeyin-pocket block. A.koeyin-pocket block
A connection to the corresponding PITreader. The quantity is limited: (PNOZ m B1: <= 4, PSS u PLC: <= 10).
Set the minimum permission required for Check-in in the login list. Access of unauthorized personnel could be restricted in this regard.
LED button input confirmation, so as to achieve "check in", "check out" process.
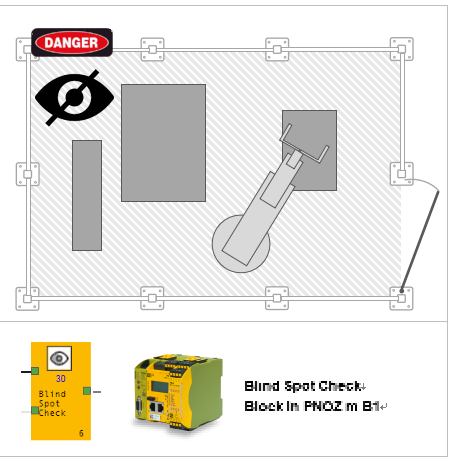
The input of "check out condition" (for blind spot checking). If the blind spot check function needs to be implemented, the input signal is given to the input point after the blind spot check is performed.
Output for Enable (list is empty) and Enable Blind Spot. Output condition for whether the device can be restarted.

B.ind spot check block B. Ind spot check block
To ensure that no one is in the invisible areas, you can configure the "blind spot check" feature.
This means that the last person to "check out" must double-check the unseen location to confirm that the blind spot is empty. (via the button and/or the specified PITreader).
This function is combined with a timer (minimum 30s) time, so the operator must complete the "check out" procedure within a certain time.
This feature can also be cascaded, i.e. multiple "blind spots" can be run and verified.
C.elete Safe Sign In List block Deletes the safe sign in list block
If an operator cannot find his or her personal key after "checking in," or if an operator has "checked in" and brought his or her personal key home, the system must be restarted by deleting the security check-in list.
The person with the minimum permissions defined can perform this list deletion. The other requirement is that the person is also registered on the secure login list.
After the check-in list is deleted, the system remains in the state that the last worker was "checked in," and then the checkout process must be performed again.
Operators may still need to perform blind spot checks.
